Internet security is becoming increasingly important – We will discuss in this article – “how companies get hacked”. We all want to move on with the digital transformation train, get online, sell online, build a website. Then you hear the story about the personal details of 24 million people being compromised through a data breach at Experian. How can you be safe, if major organisations like Experian still get hacked.
This article will have you covered, first we will start by explaining the major types of methods hackers use to get access to your information. We will discuss the obvious and not so obvious ways, you might overlook.

What is hacking?
Imagine you live in a house with a door. You gain access in to your house by unlocking the front door and locking it behind you. Inside your house, you have valuable information and property you would like to protect.
Brute force
A criminal might notice your house and decide, they want to gain access and steal what you have inside. How would they gain access? They could go to the shops, buy all possible key combinations to your door and try them all until they find a key that works. This is actually one of the oldest and most used method by hackers. Up to 5% of all confirmed data hacks in 2017 were a result of brute attacks.
This is a common methods because it works, a hacker can just run a program on the login page that tries millions of passwords until they find the right one, a way to protect yourself against this type of attack is to change your password regularly (3 months is recommended and use complex passwords, a letter, words, mixed cases, special characters and use long passwords).
Steal
A thief can simply just steal your key – by tricking you in to giving it to them or without you even noticing how they stole it. We will focus on how hackers “steal your keys” in this article.

Phishing and Smishing
Phishing is when hackers send you emails that look like legitimate messages from your bank, or the account they are trying to hack. They might cause you to worry by alerting you to a potential fraud or theft, or warn you that your account is being reviewed or cancelled for whatever reason. They key is, they request you to provide certain information to resolve the matter.
Hackers might send you to a different website using a link, all the information you enter on this new website is sent to them and that is how they steal it. Smishing is similar in that, the hackers obtain this information through a phone-call. They will call you and pretend to be from your bank, service provider and request you to verify certain things on the phone.
This is quite effective for hackers because they can sound legitimate, in some cases they already have partial information they use to convince you they are legitimate.
You must never provide any type of information through the phone to a caller, never click on links for any reason send to your email.
Malware, Trojan, Virus
If we go back to our example. This is the equivalent of the thief sending a kid to your doorstep to sell you cookies, you think this child is so cute and let them in your house. While they are inside, they open the backdoor to real criminals who steal from you.
These type of malware can be found in:
- Porn websites
- Free watch-series-online websites
- When you download pirated software, you don’t want to pay for
- Free mp3 downloads websites and apps
- Job search websites [this surprised me at first]
There are many types of malware, and this is the hardest type of thief to detect. The malware can do damage to your computer or just spy on you, even turn on your microphone and camera to record you without your knowledge.
Mobile Apps
Yes, mobile apps. You are probably surprised to see this here, but mobile apps are developed by private individuals and companies with their own motivations and intentions. As an app developer I know all the things I can write in to a mobile app, if people knew – they would never download another app.
I will give you an example:
I can create a “Restaurant recommendations app” which suggest restaurants close to you beased on your location. When you download the app, you will be asked once to grant permission for your location to be shared with the app, most of us do not hesitate. The app will not work without it, and you really want that restaurant recommendations and discount vouchers.
But, In addition to making recommendations – I can also write it in the app, that the app sends me a detailed location profile of your movements. Apps are ideal for tracking people because, you keep your mobile with you – everywhere you go. I can even write the code such that, the app is sending me data, even in the background.
I can even hide the app so that you don’t see it anymore, you even forget you once installed it. It is ridiculous what app developers can do with your phone, if in doubt use the web version of a service and avoid installing actual applications on your device.
Internet Cafes, Insecure Networks
As a rule of thumb, just avoid using internet cafes or “free wifi” at the airport, mall at all times. Keep your bluetooth always off. If you need to use it, switch it on – use it and switch it back off.
Passwords Do’s and Don’ts
- Never email your passwords. This is common when you want to share your password with a developer, someone managing your social media. I tell my clients, let us talk – you tell it to me and then we change it later. Never send it via email.
- Everyone knows this but are lazy to change it – Do not use the same password everywhere. Rather keep a list and write them all down.
- Do not write your passwords in a file on your computer. I know so many people with a note called “passwords” and they write all thair passwords there. Don’t do it.
- Always use 2-Factor authentication. Most services that require security have the option, but do not enforce it. Always request a method of 2FA. Make the job harder for the hacker – they must now hack two systems to get to you.
- Change your passwords every 3 months, someone probably has a brute force program running on you now. So change the password and confuse the enemy.
Recovery Plan
Recovery plan. At some point or another, you will get hacked. Prepare for it – consider all the options and alternatives. What will you do? how will you recover – is your information backed-up? Do you have insurance?
Security System
Get a good security system, better pay R300 than lose 10-100 times that amount in a hack.
An antivirus can protect you against all known threats, key-word here is known: malware, spyware etc. Criminals are always coming up with new things, the best you can do is deal with the known threats for now.
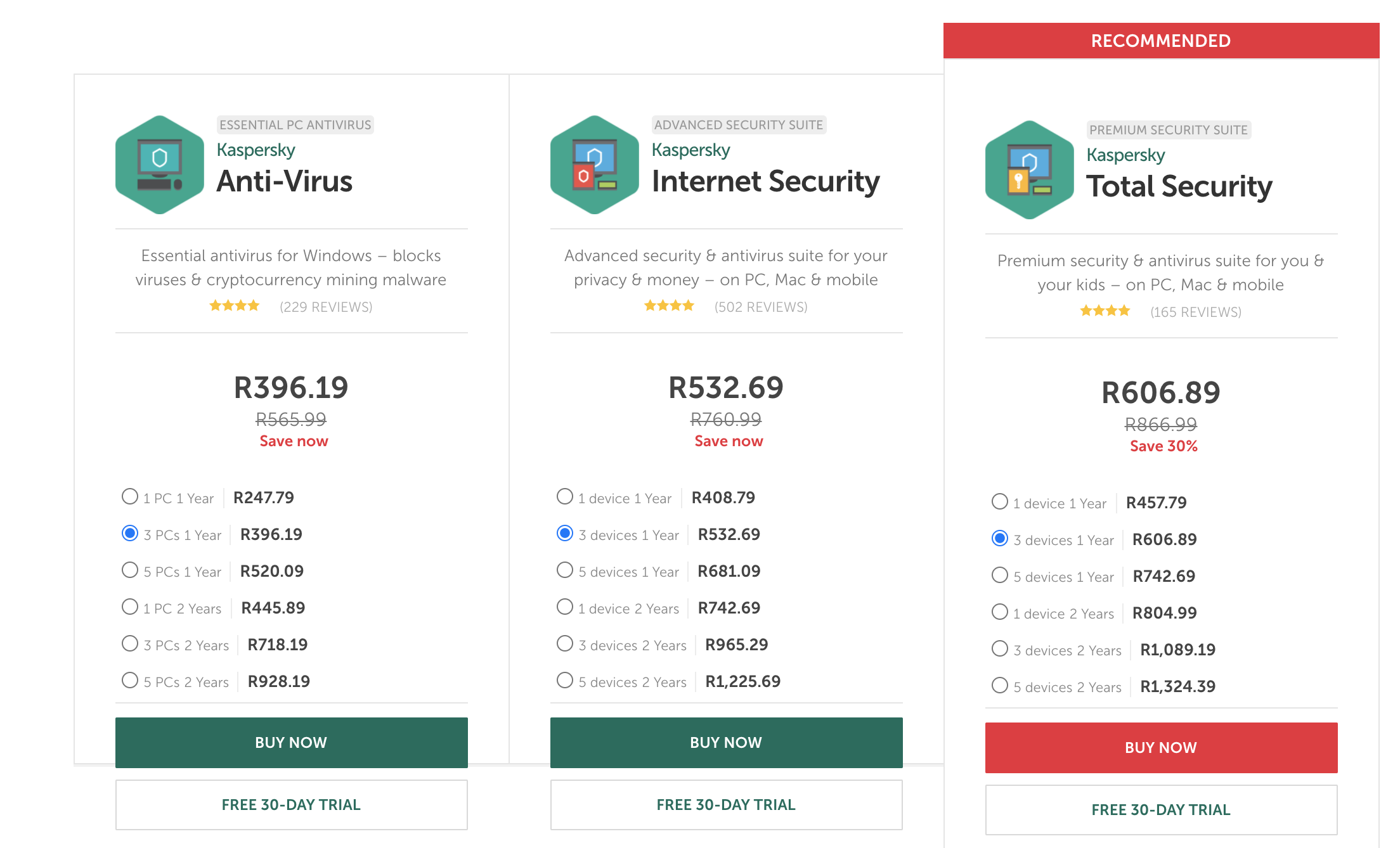
You never recover from your hack, in some cases you might have to change entire email addresses, phone numbers. This is because hackers share information between each other. If someone hacks you once, you are tagged and many more will try you – because your information is probably already shared 100 times over on the dark web as a soft target.
Now that you have an idea of how companies get hacked, try implementing some of these solutions to protect yourself online.
If you would rather watch the video:


Leave a Reply